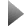Cyber Command Center Complex Incidents
View Complex Incident History
Impact Level
Significant
Significant Minor
Significant
Incident Type
DNS/Phish Attack Robot.txt Recon
Data Exfiltration Denial of Service Data Exfiltration
Contributing Events Event
DNS Cache Poisoning Event
Multiple outbound connections to hostile host
Email containing Poisoned DNS Cache entry
Event Info EVENT:
ID Number
Incident Date
DNSP-246 05 May 09
Process Status
Pending
Last sign-in:
Network Selector National Capital Region Current Incidents: 7
Assigned To
Watcher, John
RTR- 458 04 May 09 In Process Seer, Jane DE-78
DOS-459 03 May 09 Pending DE-78
Recommended Courses of Action Category Location
Security Security Security
Andrews, MD Langley, VA Washington, DC
Source Info Destination Info Potential DNS cache poisoning attempt Attention:
If you have determined that this event should be disassociated from this Complex Incident, enter the reasons why and confirm.
Time Stamp
13:12:34 23 Jan 09
12:13:39 24 Jan 09
13:12:34 21 Jan 09
Notes Virginia West Andrews Virginia Langley CONFIRM
District of Columbia
Pennsylvania New Jersey McGuire Maryland Dover
04 May 09 Informational Roscoe, Bob Watcher, John
02 May 09 In Process Watcher, John Last Update 06 May 09
Updated By
Watcher, John
07 May 09 Seer, Jane 06 May 09 Roscoe, Bob 04 May 09 Watcher, John 02 May 09 Watcher, John
National Capital Region New York Connecticut
John J. Monitor Select From My Links
Incident Impact Technical:
2 Servers, 6 routers down
Operational/Mission: Golden Toothpick
Major Impact Peanut Day
Significant Impact Battle Damage Assessment
Internal Incidents Being Monitored 22%
Denial of Service DNS Cache Phishing Attack Data Exfiltration Excessive IDS Other
33% 22% 19% 13% 10% 3%
19% 33% 3% 10%
Cyber Control System Increment-1, shown as a mockup, will help Air Force officials provide mission assurance to about 845,000 users. (below) Cyber Flag 14-1 participants analyze an exercise scenario at Nellis AFB, Nev.
13%
ly by computer. The generator caught fi re and was destroyed. Although attempts have been made to secure critical elements of government and commercial infrastructure since then, many systems remain vulnerable. In FY 2013, the Government Account- ability Offi ce reported 46,160 cyberat- tacks on federal agencies alone. Some of the most vulnerable net-
works are the supervisory control and data acquisition systems that often
66 MILITARY OFFICER JANUARY 2015
control water, power, and other infra- structure elements. They can be lo- cated in remote areas and accessed by telecommunication links, which some experts think makes them vulner- able to cyberattack. In addition, many use off -the-shelf software that can be modifi ed by intruders.
A covert invasion While a physical full-scale attack is meant to create as much “shock and
IMAGES: ABOVE, AIRMAN 1ST CLASS CHRISTOPHER TAM, USAF; TOP, COLIN HAYES BASED ON U.S. AIR FORCE PHOTO ILLUSTRATION
 Previous Page
Previous Page